CyberSavvy Center
Fundamentally change the game in computer protection –Turn Computer Security from Art into Science and Engineering
Sponsor
We gratefully acknowledge the support of the Defense Advanced Research Projects Agency (DARPA) CPM Program.

What We Do
Problem:
Our computers are insecure and too easily compromised, but they are managing everything in our modern society (business, communications, transportation, appliances, health…). Today’s computers cannot tell good from bad; they are unable to differentiate intended use vs. abuse. As a result, they are too easily fooled into working against the owner of the system and their intent. At best, today’s security is a poorly practiced, undisciplined art. Today’s computer systems design approach leaves protection to every individual contributor—we just ask each programmer to write bug free software and hardware at every level—even as we continue to grow the size of our systems. Any bug in any component has the potential to compromise the security of the whole system. Fundamentally, the advantage goes to the attacker—the attacker only needs to find one flaw, while the defender must make sure every component and line-of-code is flawless (does not allow unintended use).
Goal:
Change the game in computer protection, making computers worthy of the trust we place in them and turning security into an engineering discipline.

Engineer high security systems designed for today’s technology, stakes, and threats:
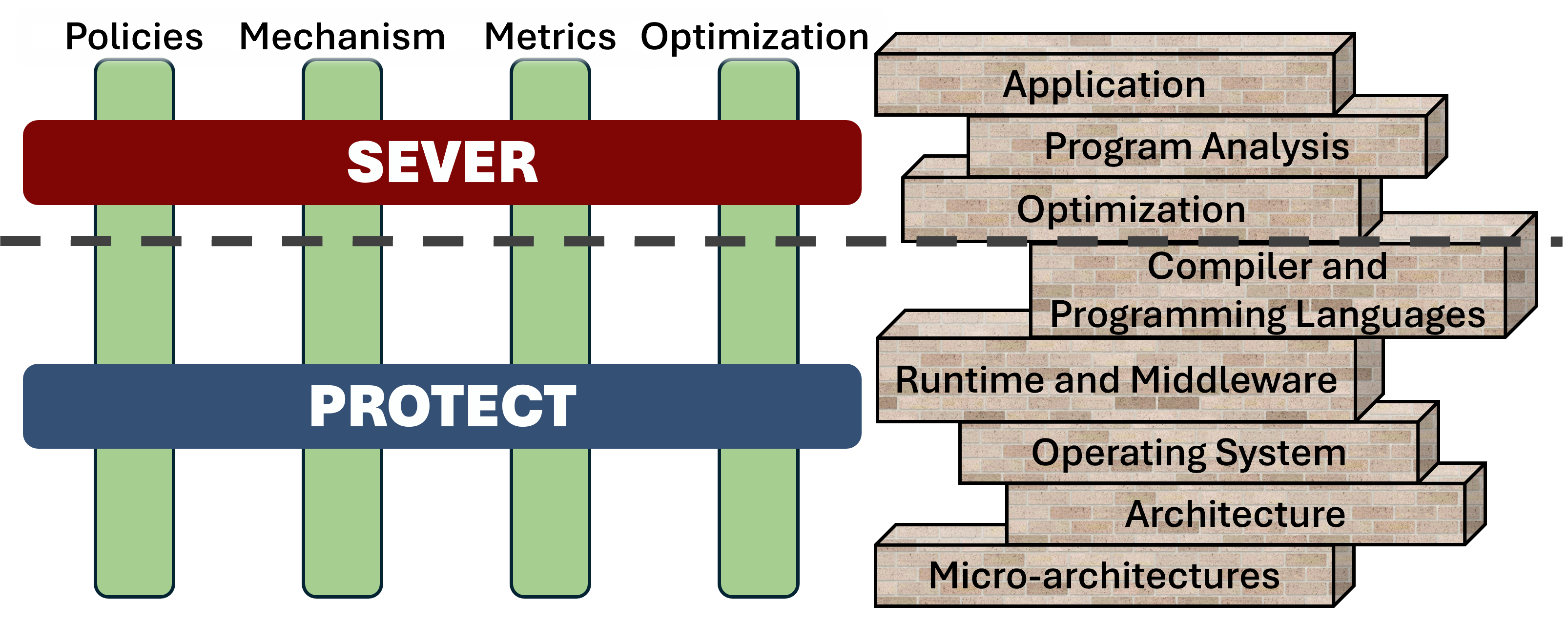
We introduce four fundamental elements of a new engineering discipline to support this goal: mechanisms, policies, metrics, and optimizations.
Mechanisms
To flexibly and efficiently enforce a wide range of security policies and abstractions, we co-design hardware-rooted mechanisms across the stack. Our hardware-rooted mechanisms embrace and exploit now inexpensive silicon resources, working with the system software, to enforce foundational security policies and OS/programming-language abstractions without compromising performance and without discarding all the software and systems that exist today. Our mechanisms are expressive and flexible to support new policy innovations to adapt to threats and lessons and to support system tuning and optimization. Our cross-stack co-desgin solves problems at the right level in the system for a given technology and system goals while not leaving seams and weaknesses between layers that undermine enforcement.
Policies
We develop policies and invariants that apply broadly to systems. We use our policies to embrace known security principles and develop ways to systematically enforce them throught out designs, including Principle of Least Privilege, Separation of Privilege, and Complete Mediation. These policies can take whole classes of bugs or vulnerabilities off the table. This is in stark contrast to patches that fix individual instances of a bug.
Metrics
We develop quantitative metrics to guide security improvements. These move us beyond “expert” opinion toward a science and engineering discipline for security. We quanitfy exposure and risk to guide developers and optimization tools. These metrics must be mechanically and objectively computable.
Optimizations
We bring automated optimization to program and system security, rather than relying soley on expert-intensive, manual program refactoring. This gives the opportunity to rapid explore a large continuum of design options rather than a single, manually defined design point. We can exploit computations, optimization algorithms, and search to find favorable security and performance points in the design space. This further allows us to rapidly adopt to changes in goals, threats, system configuration, and hardware and system costs, with minimal human effort.
SEVER and PROTECT
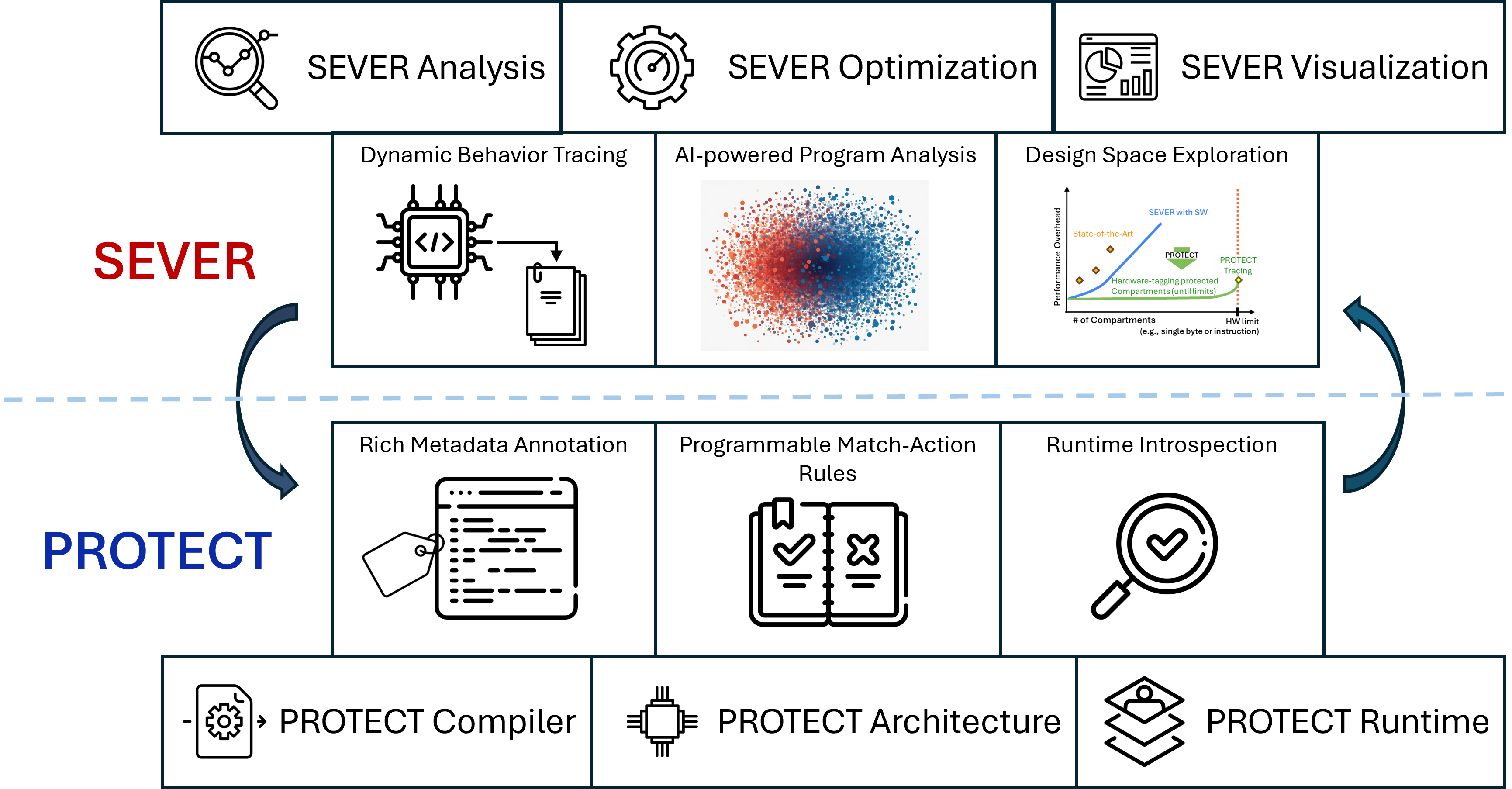
In an age where cybersecurity threats are growing more sophisticated by the day, a pioneering research collaboration between the University of Pennsylvania and Draper Laboratory, is on a mission to revolutionize how we trust and secure our computers. Their ambitious goal? To make computers trustable by fundamentally reducing the excessive privileges that often lead to vulnerabilities.
The Principle of Least Privilege: A New Security Paradigm
At the heart of this initiative is the Principle of Least Privilege, a security concept that demands each program, user, or system component be granted only the minimum access necessary to perform its function. Consistent with the Cybersavvy Center goals, this effort advocates for a shift away from the traditional approach of assuming all system components are benign and all programs are free of bugs. Instead, they operate under the assumption that any component could be malicious/exploitable, and software bugs are a given, not an exception.
This security-first mentality is more than just theory. The project’s researchers are putting it into practice by focusing on protecting the Linux kernel—a critical component of countless operating systems—and safeguarding applications from exploitation.
Innovative Approach: Making Compartmentalization Accessible
To achieve their goal, the lab is breaking new ground in the realm of fine-grained compartmentalization. Compartmentalization, in simple terms, involves breaking down systems into isolated sections to limit the damage from potential breaches. What makes this lab’s approach unique is their use of Tagged Architecture, which promises to make this complex process more cost-effective and accessible.
Their work builds on foundational projects like the Software-Defined Metadata Processing (SDMP) and DOVER. These projects serve as the backbone for the lab’s efforts, PROTECT effort that provides an efficient mechanism for fine-grained separation. ensuring that their solutions are not only innovative but also grounded in proven research.
Balancing Security and Performance with Automation
A key innovation of this project is SEVER effort with its ability to automatically create security compartments while maintaining a delicate balance between security and system performance. They build on metrics and optimization like uSCOPE and SCALPEL to manage and analyze micro-privileges within the system, ensuring that security enhancements do not come at the cost of performance.
DARPA: Supported
This research is supported by
DARPA, specifically under the Compartmentalization and Privilege Management (CPM) program.
In conclusion, this research is not just addressing the cybersecurity challenges of today; it is laying the groundwork for a more secure digital future. By reducing excessive privileges and embracing innovative technologies, in ensures that our computers can be trusted in an increasingly perilous cyber landscape.
Standards and Interfaces
- CPM Compartmentalization File Format Draft – Work-in-progress draft for expressing software compartmentalizations and dynamic trace feedback.
Contact
We are actively looking for graduate students, postdocs, and staff.
- cybersavvy@seas.upenn.edu
- 200 S 33rd St, Philadelphia, PA 19104

